Man-in-the-Middle
Man-in-the-Middle/Email Spoofing
The English term spoof literally means “parody” or “satire.” In computer science, this term is used to describe a very broad category of attacks, all characterized by having as their object the falsification of information.
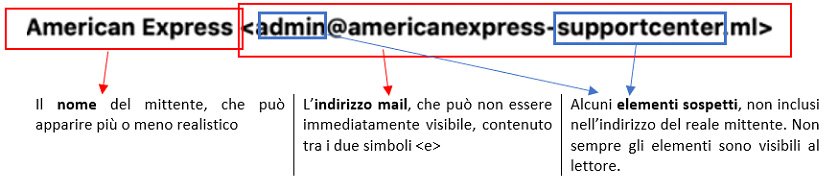
The email spoofing technique consists of altering and/or forging an email address to deceive the recipient about the origin of the message.
A spoofed email address usually appears as follows:
The immediate purpose of email spoofing is to deceive the recipient into believing that he/she knows the sender or, at the very least, that he can trust the sender (a colleague, a supplier, a company). Consequently, this technique is mostly used in phishing.
Usually, with a normal email client (e.g., Microsoft Outlook), it is not possible to enter the sender’s email address, which is automatically generated when creating a new email or responding to an email received. However, there are programs that allow you to change the sender’s address by creating an ad hoc one. In this way, the recipient will read an email address that, however, is only a “facade.” The email, in reality, comes from another address, not immediately visible.
The immediate purpose of email spoofing is to deceive the recipient into believing that he/she knows the sender or, at the very least, that he can trust the sender (a colleague, a supplier, a company). Consequently, this technique is mostly used in phishing.
Usually, with a normal email client (e.g., Microsoft Outlook), it is not possible to enter the sender’s email address, which is automatically generated when creating a new email or responding to an email received. However, there are programs that allow you to change the sender’s address by creating an ad hoc one. In this way, the recipient will read an email address that, however, is only a “facade.” The email, in reality, comes from another address, not immediately visible.
How to recognize an email spoofing attempt?
It can always be useful to look carefully at the sender’s email address to retrace any extraneous elements that may raise suspicions about the legitimacy of the address. There are multiple systems that are routinely used:
⦁ SPF (Sender Policy Framework) system, which can be set up to identify IP addresses authorized to send email on behalf of a domain.
⦁ DMARK system, which is useful for blocking malware and phishing attacks and can be configured to send periodic reports.
⦁ anti-spam and anti-phishing software.
Man-in-the-middle (MITM) is a particular type of cyber-attack characterized by the fact that a malicious party inserts itself into the Internet traffic between two parties who remain unaware of the presence of the third party. This gives the malicious user the opportunity to intercept, divert and manipulate communications, changing their content and representing untrue situations to the two targets.
The purpose of such an attack is easily guessed: to obtain data and information from targets, to share malware and viruses, and, in general, to deceive victims for your own ends.
An MITM attack can, with a good degree of approximation, be represented as follows:
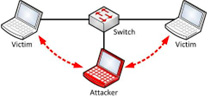
The victims are convinced that they are communicating with each other. In reality, each of them sends their own message to the malicious user, who modifies it and forwards it to the other victim, pretending to be the former. To carry out such actions, the malicious user inserts himself into a communication through specific software and uses spoofing techniques to deceive the receivers about his own identity.
We can distinguish different types of attacks depending on the target environment of the malicious user:
- man in the Wi-Fi: when the malicious user compromises a wi-fi network (typically, a public network, such as that of trains, public hotspots, etc.) and intercepts communications that take place by exploiting this network.
- man in the browser: implemented through the installation of malware on the victim’s computer, it allows the malicious user to modify online activity (typically, transactions) made by the victim, without the victim being aware of it.
- man in the IOT: characterized by the malicious user’s collection of data through insertion into the protocols of objects connected to the Internet, which are also often used as gateways to more complex systems.
- man in the cloud: these are attacks that target online sharing systems (Dropbox, OneDrive, Google Drive, etc.). Malicious users infiltrate the cloud to steal data and documents and upload malware.