Checks and constant revision
One of the most common mistakes in IT and information security management is to regard it as static without needing adjustments and corrections over time.

The danger inherent in such an approach – which is particularly common in the context of poorly structured or small companies and organisations – is essentially that of ignoring the very rapid changes in threats and attack techniques, thus depleting the security safeguards in place and exposing data and information to risks that are not adequately managed.
The approach to computer and information security is, in reality, an entirely dynamic process, which must therefore have as its guiding star the goal of continuous system improvement, effectively summarised in the concept of the PDCA or Plan-Do-Check-Act cycle.
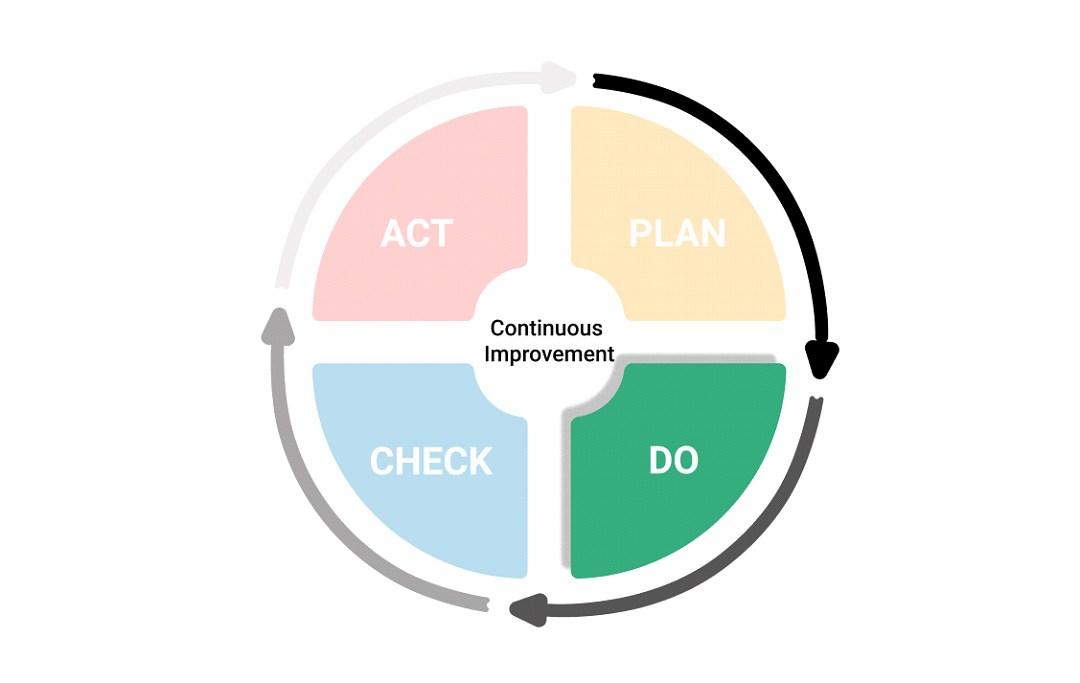
(Plan), i.e. identifying the activities, processes, and tools to be used to achieve the set objectives (in our case, the security of data and information processed by the organisation)
(Do), i.e. implement the planned activities
(Check), i.e. to check at periodic intervals or in the presence of relevant events, the effectiveness of planned and realised actions concerning the defined objectives
(Act), addressing any deficiencies found in the verification phase
The verification and intervention phases are, therefore, of particular importance.
In particular, verification activities should be defined at the planning stage to determine their timing and modalities – for instance, by providing periodic checks to verify the constant adherence to the security measures adopted concerning the defined risk level. Verification activities, in particular, can take very different forms and methods. However, usually, in more structured contexts, verifications occur through inspections and audits, either internal or conducted by external consultants (so-called second-party audits) or by certification bodies (so-called third-party audits, shown, for instance, by the ISO 27001 certification body).
The intervention phase, aimed at ‘rectifying’ the shortcomings and non-conformities detected. It will thus be all the more effective, the more frequent and detailed the verification moments are.